High Assurance Intelligent Infrastructure Toolkit: Program Results
21st Oct 2021
Program goals
The High Assurance Intelligent Infrastructure Toolkit (HAII-T) Program deals with the menaces to the security of the modern, smart infrastructures. Intelligent infrastructures are objects of extreme complexity (aka systems of systems) which are difficult to protect and, contemporary, very appealing for an attacker.
The cornerstone of the HAII-T Program is that security must be considered along the entire life cycle of an infrastructure, starting from the very initial design fases. This apporach aims at supporting state-of-the-art best practices such as Security- and Privacy-by-Design. The toolkit is an integrated, extensible platform that follows the development phases of an infrastructure and, at each phase, provide the right tools for dealing with the relevant security aspects.
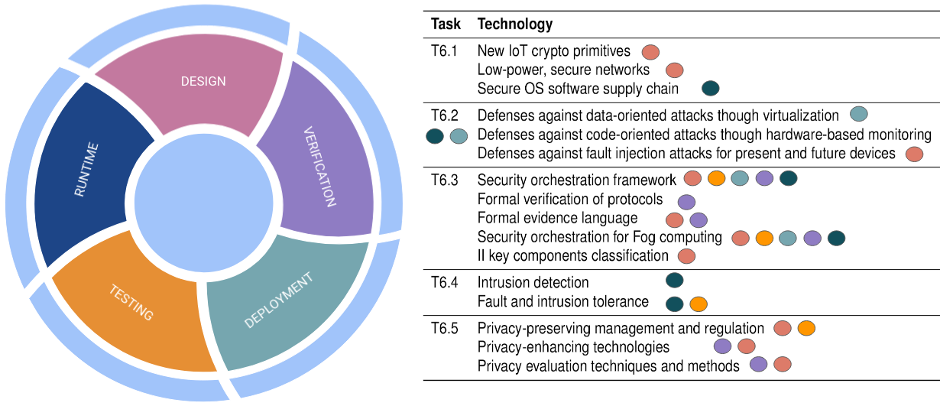
Ongoing activities
Hardening legacy components
We have started looking into reducing the attack surface of OS kernels by means of static program analysis, we are working on a prototype for reducing memory corruption vulnerabilities introduced by programming mistakes when managing dynamic memory, lightweight isolation solutions for hardening unikernels, and automated vulnerability detection in hypervisors via fuzzing. Also, we have built automated analysis and instrumentation solutions for deploying CFI mechanisms on embedded firmware. And finally, on the physical attacks front, we have analyzed various fault models induced by fault injection attacks against microcontrollers and we have made a study on software countermeasure to mitigate them.
Secure orchestration
We carry out a systematic integration of many technologies that support the creation and protection of smart infrastructures. These technologies are not designed to work toghether and, by defauld, they cannot communicate. For this reason, we created a secure orchestrator aiming at synergically compose the existing security solutions. The orchestrator allows for the design of an entire infrastructure, including IT neworks, software, hardware and even human agents. Also, it supports customizable workflows that combine several security tools in a single pipeline. Each workflow takes care of a specific security aspet during one or more phases of the infrastructure life cycle.
Privacy-by-Design
The privacy-by-design task carried out a comprehensive analysis of current and quantum-resistant privacy-enhancing technologies. Also, this activity resulted in a book chapter entitled “Privacy-by-Design in Intelligent Infrastructures” which is focused on legal and technical aspects in privacy protection. In practical activities, we focused on the development and integration of PETs into intelligent infrastructures, for example, the Privacy-Enhancing Authentication System (PEAS) that is based on the attribute authentication scheme, the m-DIEX Multi-client Searchable Symmetric Encryption based on the IEX scheme which enables to perform a blind statistical analysis of service transaction data and the DPO tool (https://dpotool.cs.ut.ee/) that supports the process analysis for checking GDPR compliance.
Assets and demos
Among the results produced by the HAII-T Program, two are of particular interest. The first one is a common case study inspired to a real intelligent infrastructure. The case study is publicly available (on demand) and accessible both in the form of a virtual machine or through remote access to a server hosting it. A demonstration of the case study, as well as the security use cases it includes, is available at https://sparta.eu/demos/secure-orchestration-demo.html
