An ambitious roadmap
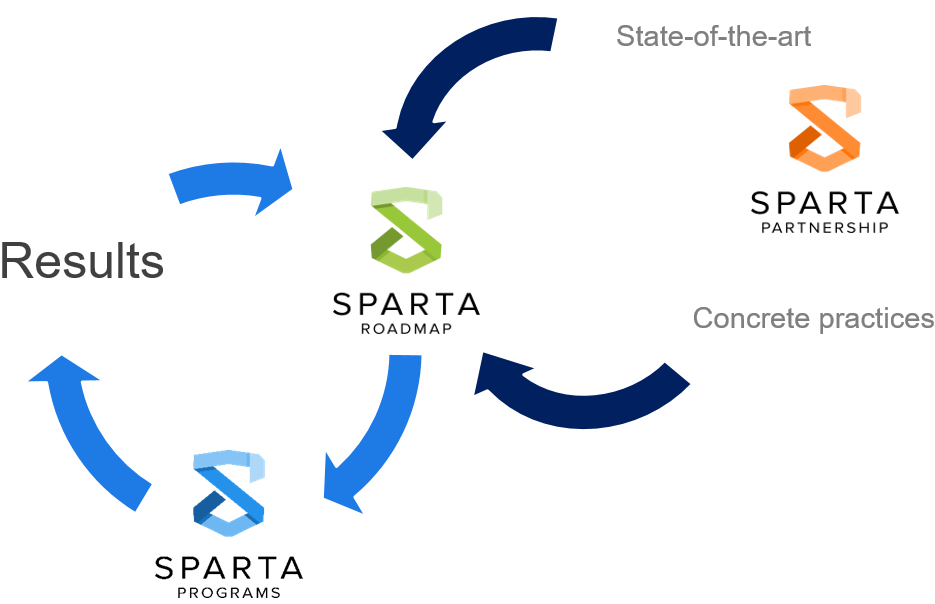
SPARTA establishes a strategic research and innovation roadmap to stimulate the development and deployment of key technologies in cybersecurity and to retain digital sovereignty and autonomy of the European industries.
SPARTA Roadmap serves as common ground for the alignment of research, education and certification priorities of the European Cybersecurity Competence Network.
Emerging challenges
SPARTA roadmap also contains an open-ended list of emerging challenges. For the first version of the roadmap this list includes User-Centric data Governance, Autonomous Security for Self-Protected Systems, Trustworthy Software.
In a second iteration of our roadmap process, we also added three new challenges: Quantum Information Technology, 5G Security and Next-Generation Computing Architectures.
Inputs are collected from interested parties from industry, academia and governmental institutions. It is developed in concert with national and European research agenda (e.g. ECSO) and is structured following the European Joint Research Centre's taxonomy for Cybersecurity.
Research programs are continuously spun from strands of the roadmap, led by experts of their fields, and aim at generating concrete and transformative results.
SPARTA created four programs extracted from the SPARTA Roadmap at the beginning of the project and feeding it with new challenges and ideas.
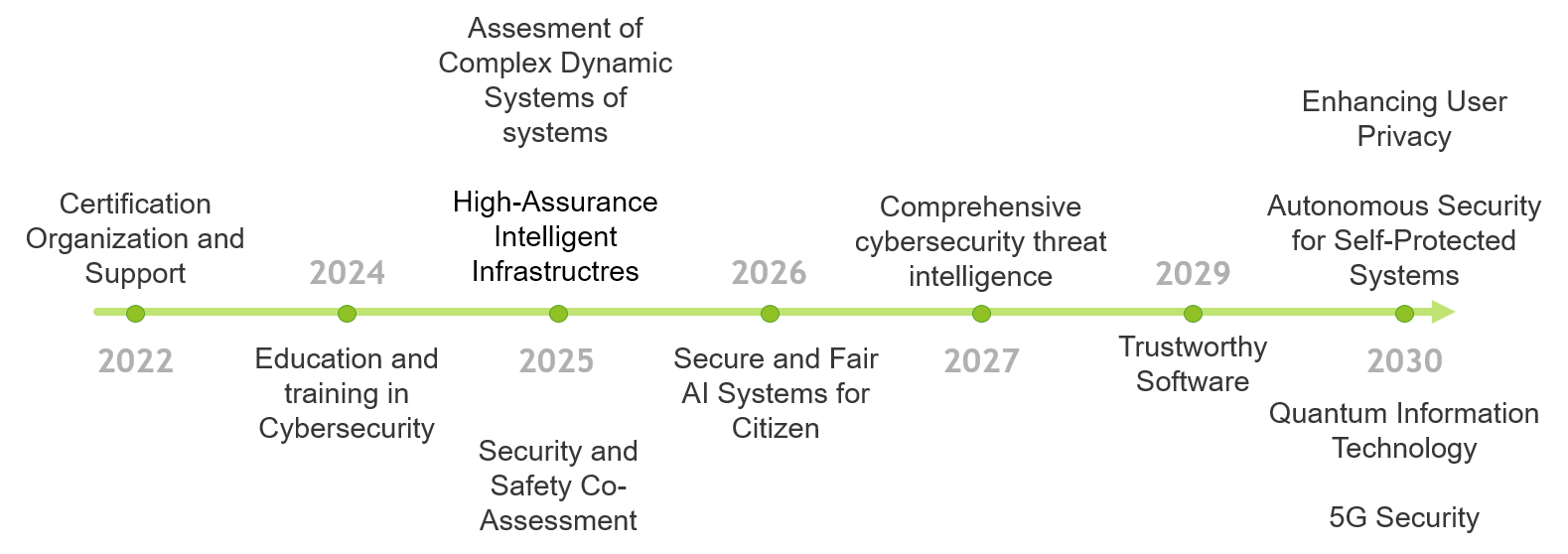
Roadmap Timeline
-
2022
Certification Organization and Support -
2024
Education and Training in Cybersecurity -
2025
Assessment of Complex Dynamic Systems of systemsHigh-Assurance Intelligent InfrastructuresSecurity and Safety Co-Assessment -
2026
Secure and Fair AI Systems for Citizen -
2027
Comprehensive cybersecurity threat intelligence -
2029
Trustworthy Software -
2030
User-Centric Data GovernanceAutonomous Security for Self-Protected SystemsQuantum Information Technology5G Security
-
Certification Organization and Support
2022
-
Education and Training in Cybersecurity
2024
-
Assessment of Complex Dynamic Systems of systemsHigh-Assurance Intelligent InfrastructuresSecurity and Safety Co-Assessment
2025
-
Secure and Fair AI Systems for Citizen
2026
-
Comprehensive cybersecurity threat intelligence
2027
-
Trustworthy Software
2029
-
User-Centric Data GovernanceAutonomous Security for Self-Protected SystemsQuantum Information Technology5G Security
2030
Certification Organization and Support
2019-2022
Problem description
Given the growing threats that connected systems face, it has become important to protect IT-based infrastructures and systems sufficiently. Cybersecurity certification is one way to help engineers design more secure systems. Over the years, many cybersecurity standards and certifications schemes have been created at both European and international level. In the context of the European digital single market, it is important to have a simple cybersecurity certification scheme that is recognized throughout all European countries. To move in this direction there is a need to analyse different national European cybersecurity initiatives as well as international efforts in order to identify commonalities and differences. Standards and certification schemes can be classified in different ways. Some standards and schemes have been designed for products and others for processes and services. Other standards are sector-specific such as in transport or aeronautics. Others focus on specific technologies, e.g., networks or cloud computing. More widespread adoption of cybersecurity certification in the design of connected products and services will be successful only if certification is perceived as cost-effective and that it effectively improves the quality of products and services. For certification to be more widely adopted in security engineering, there is a clear need to design more agile certification processes, to better integrate certification in the security engineering process, and to improve the effectiveness of certification schemes.
Industrial demand: The EU cybersecurity certification framework will be voluntary and not mandatory. It will be up to sectorial certification schemes, e.g., for critical infrastructure and 5G, to define whether certification is mandatory or not.
Social aspect: Clients of systems are becoming worried about cybersecurity threats and are asking that systems be more thoroughly tested for cybersecurity. This is particularly true for industrial systems in critical infrastructure with strong safety requirements.
Benefits for EU: European systems and services that are well protected will contribute to the image of quality for European products and services.
Domain (JRC Taxonomy): Assurance, audit and certification
Sector (JRC Taxonomy): All sectors
Relation to emerging technologies: Artificial intelligence can be used by to attack and to protect systems from attack.
Education and Training in Cybersecurity
2019-2024
Problem description
Individual academic and professional programs are already available at many universities and training institutions, but there is a lack of coordination and understanding, what courses and topics should be included in these programs so that they reflect the current trends on the job market.
Industrial demand: The demand for cybersecurity experts is extraordinary internationally, both at companies and in the public sector.
Social aspect: By providing top-quality education in security, graduates get high-qualification jobs more easily and employees can reach to higher positions in their respective jobs.
Benefits for EU: Better competence in cybersecurity, more secure ICT environment, better protection against external threats, and the more balanced situation on the job market.
Domain (JRC Taxonomy): Cybersecurity education, Cybersecurity exercises, Cybersecurity ranges, Cybersecurity education methodology, Certification Programmes.
Sector (JRC Taxonomy): Government and Public Authorities, Publishing, Internet
Relation to emerging technologies: Cyberranges, Gamification
Assessment of Complex Dynamic Systems of systems
2020-2027
Problem description
IT services are increasingly complex and dynamic, as exemplified by the DevOps paradigm. They also increasingly rely on third-party services, either transparently (such as name resolution or routing at the network level), or explicitly (such as single sign-on provided by major Internet actors to smaller entities). On the other hand, assessment and certification processes are static, long and expensive. Therefore, it becomes increasingly difficult to evaluate and certify interdependent complex systems that constantly evolve and receive new functionalities. This implies that the target of evaluation is undergoing constant evolution. The challenge is thus to 1) define and publish the appropriate cybersecurity properties, 2) assess that these properties are met by increasingly complex and dynamic systems and services, and finally 3) certify compliance with these cybersecurity properties as well as regulations, in a way that is verifiable by providers and customers alike. This must happen all along the lifecycle of these products and services, from design to retirement. It must be robust to either runtime changes or lasting modifications, ensuring that assessment (and certification) evolves at the same pace as services. The focus of this challenge is on cybersecurity for complex digital infrastructures, offering e-services. Even though these digital infrastructures might be driven by physical processes, safety and resilience aspects are treated in the second challenge of the CAPE program.
- Modelling of the properties of complex systems
- Automated assessment methods and tools
- Incremental assessment methods and tools
Industrial demand: Automation of assessment and certification, leading to better stability of systems and services, as well as non-regression.
Social aspect: Better stability of systems and services, leading to increased trust and use.
Benefits for EU: Support to the development of EU-based champions; better management of the supply chain when sourcing products and services outside of the EU, to better support European requirements and values.
Domain (JRC Taxonomy): Assurance, audit and certification
Sector (JRC Taxonomy): All sectors, with a focus on IT aspects of all these sectors.
Relation to emerging technologies: Artificial intelligence, Machine learning, Big data
High-Assurance Intelligent Infrastructures
2020-2025
Problem description
As small, connected devices evolve from being an Internet of Things (IoT) towards a true intelligent infrastructure (II), vulnerabilities in such devices become more and more critical.
Industrial demand: There is a huge market for IIs in a variety of domains, e.g., manufacturing, transportation, domotics, health & well-being, smart-cities. While the industry devoted to the manufacturing of hardware and software components for individual components (sensors, actuators, networking) is thriving, the full potential of IIs will be achieved only through the provisioning of a secure-by-design development framework for large-scale II.
Social aspect: IoT technology is already threatening the users’ privacy. As society will become more and more dependent on IIs, the availability of IIs is also bound to become a natural target for attackers. IIs are also likely to become a powerful attack vector (cf. Mirai attack). IIs will be widely accepted by society only if the security of their functioning will be ensured. Applied privacy-enhancing technologies as a part of a privacy-by-design framework will increase the trustworthy of IIs and IoT services and applications in society.
Benefits for EU: Virtually all industry sectors in the EU would gain a competitive edge with this technology, as it would enable them to offer secure products to the market. Additionally, the products will be natively in line with privacy regulations and standards.
Domain (JRC Taxonomy): Security, Audit, and Certification; Cryptology, Data Security and Privacy; Identity and Access Management; Network and Distributed Systems; Software and Hardware Security Engineering; Theoretical Foundations; Trust Management, Assurance and Accountability
Sector (JRC Taxonomy): Energy; Government and Public Authorities; Health; Maritime; Tourism; Transportation; Smart Ecosystem; Supply Chain; Public Safety
Relation to emerging technologies: IoT; Mobile devices; Edge Computing
Security and Safety Co-Assessment
2021-2025
Problem description
Systems and services are increasingly relying on connectivity for operations, typically command and control. This means that if adequate counter-measures are not put in place, these systems may be vulnerable to cyber-attacks that can cause catastrophic events, e.g., human and environmental losses. In order to prevent these events, it is necessary to ensure that safety properties are not adversely impacted by a cyber-attack. Therefore, it becomes necessary to include cybersecurity properties in the specification and assessment of safety properties. In the automotive domain, the deployment of applications and services must include security and privacy requirements to protect critical functions such as driver assistance, collision warning, automatic energy braking, and vehicle safety communications. Cyber-attacks on these functions can cause accidents and therefore, shall be avoided, while still maintaining the safety of the system. This is a necessary step towards the deployment of trustworthy autonomous/automated vehicles.
Industrial demand: All industrial/critical infrastructure and cyber-physical systems, in general.
Social aspect: Trust in components that are used daily, such as vehicles, building management systems, transportation, energy, telecommunication, health, manufacturing, etc.
Benefits for EU: Develop trusted components for the Digital Society. Ensure that certifications schemes meet EU needs and values.
Domain (JRC Taxonomy): Theoretical Foundation, Human Aspects, Legal Aspects, Data Security
Sector (JRC Taxonomy): Transportation, Health, Energy, Financial, Government, etc.
Relation to emerging technologies: Connected vehicle, smart mobility (building, city, transportation), collaborative robots.
Secure and Fair AI Systems for Citizen
2022-2026
Problem description
The proliferation of Artificial Intelligence systems in contemporary lifestyle brings about both astonishing benefits and brand-new challenges for society. While the gains and the prosperity delivered by AI are abundant in all walks of life, starting from most obvious ones, like image recognition, search engines, recommender systems, autonomous systems, including vehicles, to less obvious uses, like cybersecurity. The widespread adoption of AI does not consider that those algorithms were developed not taking into account the adversarial nature of real-life implementations. Thus, an array of problems emerges. First and foremost, the bulk of above-mentioned algorithms have a black box nature. This means that even though the insights provided those methods are meaningful and valuable, no one can easily explain how exactly the AI came to its conclusions. Every machine learning model, prior to applying it, has to be trained. The training can be run in any of the following three ways: supervised, unsupervised and semi-supervised. Each of them has its advantages and drawbacks and is used in different applications. While the ML algorithms invariantly fit the presented data, it is a challenging task to try to explain how specific data affects certain aspects of the algorithms, which then translates to the end result. One of the facets of the SAFAIR program attempts to address the situation by enhancing the explainability of AI. Secondly, methods exist that allow to compromise AI itself in several ways. A knowledgeable individual can influence the way an AI classifier judges a specific data point, thus evading detection. A malicious user could also provide a series of inputs in the training, or re-training phase of a classifier – in other words poison the data – to make the algorithm behave in a way that is beneficial to the adversary. Thirdly, a trained AI setup constitutes a major expenditure of expert time and therefore company resources. This makes an AI model a valuable intellectual property. There are ways, however, to fit one classifier to the output of another classifier, essentially stealing the original algorithm. Last, but not least, any bias on the AI part, especially in socially sensitive areas, could relatively easily seed distrust to AI technology among the general public. In the midst of all that, there are new cybersecurity challenges that gain ground recently. With the universal danger of cybersecurity breaches, enhancing the cybersecurity condition and detection algorithms is of absolute importance. Malware is now identified as the stern menace for commercial and critical IT systems, as well as for the general public. Malware, however, is adequately comprehended and can be dealt with sensibly well. A more menacing challenge arises, stegomalware and the use of the information hiding techniques by cyber-criminals.
Industrial demand: Every industry relying on AI technology is now vulnerable to adversarial attacks; this includes critical, sensitive domains, like automotive, government, medical fields, security-related, etc. Providing secure and explainable AI systems would increase trust in these kinds of systems, allowing further adoption, and preventing possible adversarial intrusions, hijacking of algorithms, or breakdowns. Risks are related to the various classes of assets. Structures like payment systems in the financial arena, embedded systems, cloud computing services and systems processing personal data are especially exposed to the danger of cyberattacks.
Social aspect: The wide audience needs to trust AI solutions to rely on the decisions inferred from data. The possibility of manipulation of AI breaks this trust and makes the whole big data ecosystem unreliable. Thus, AI resilient to adversaries is necessary. Appropriate use and re-use of data are mandatory for AI systems to continue to flourish. Thus, setting up systems to make AI compliant with current and upcoming data-related legislation is of utmost importance. Furthermore, establishing a track record of what is perceived by the general public as fairness with regards to how AI operates has the potential of accumulating trust to those kinds of solutions.
- Enhanced explainability and better threat understanding in AI context
- Systems using AI more reliable and resilient
- More effective methods and tools for analysis of security threats for AI systems
- A set of techniques and solutions for AI systems protection
- Systems in place to ensure fairness of AI systems
- Defensive and reactive mechanisms geared towards novel cybersecurity threats
- Cybersecurity systems being able to detect stegomalware
Benefits for EU: This kind of technology could provide EU AI industry a leading position on the global market, given the unique selling proposition of the only secure AI on the market
Domain (JRC Taxonomy): Theoretical Foundation, Human Aspects, Legal Aspects, Data Security
Sector (JRC Taxonomy): Health, Energy, Financial, Government, etc.
Relation to emerging technologies: Artificial Intelligence, Big Data, Autonomous Machinery, Robotics
Comprehensive cybersecurity threat intelligence
2020-2027
Problem description
The problem definition is complex as the topic by itself:
- Phenomena: evolution and development of cyber-attacks and exploitation of different kinds of vulnerabilities have formed new categories of cyber-threats: complex by initial design, well planned, organized over the time by several stages, having good social engineering component, having political or ideological motives and/or linkage with high value industrial or geopolitical gains. New, high complexity, threats requires new approaches and methods on how to tackle them.
- Approach: for more complex, multi-stage, full-spectrum cybersecurity incidents traditional cybersecurity function organization is not sufficient and not effective anymore. Considering this part of phenomena, detected cybersecurity incidents (ones being part of the large multistage operation), puts us in the situation where we can only fight consequences. We need capabilities to fight phenomena on early phases of multi-stage operations, meaning – moving from incidents to threats, from reactive to predictive organization of cybersecurity.
- Governing cybersecurity: to address complex, multi-stage, full-spectrum, uniquely designed cyber-attacks, cybersecurity must be organized cross-institutionally and cross-border. Single institution perimeter protection oriented cybersecurity organization is not efficient and does not provide sufficient context information in order to spot correlation, make a prediction and decide on adequate measures on early stage. We need to bring cybersecurity towards a collaborative organization.
- Data sharing: collaborative organization of cybersecurity naturally requires wider data access and data/information sharing, which is challenge by itself. GDPR and other privacy, security and confidentiality
- Concept: historically organization of cybersecurity function had more technical roots and IT perimeter security organization. Nowadays, cybersecurity is an important piece of differently targeted attacks and requires a comprehensive approach to uniting both societal and technological sides of threats to tackle them. Such an operation like Elections Interference is a combination of direct attacks, public brand and reputation attacks, information lacking, fake news, propaganda, the polarization of society, etc. Social engineering plays a more and more significant role in cyber threats therefore
- Analysis model: diverse cybersecurity information and indicators of threats are hardly incorporable into a single analytical model. Empirically we can state that in such a situation, visual analytics techniques is the way to solve it; however, which one is the most efficient for cybersecurity threats is an open question for now.
- Regulatory: organizing cybersecurity function around early phases of the kill chain, rises lots of regulatory questions and demands: how to define the threat, how to measure it, what privacy, ethical and other standards should be applied in order to maintain the balance between enforcement and individual rights.
- Legal: tackling the cyber threats – what legal framework should be applicable for the process, especially considering globality of the phenomena – most of the top tier threats are coming from abroad and originates outside the EU.
- Building comprehensive cybersecurity threats situational awareness picture
- Visual Analytics methods applied for comprehensive cybersecurity threats analysis
- Different origination and nature data sharing among diverse actors
- Cybersecurity threats analysis regulatory framework
- Legal basis for comprehensive cybersecurity threat processing
Industrial demand:
- Need for EU proprietary tools, technologies and solutions to assure top tier cybersecurity threats prevention.
- Potential application in automotive, energy, critical infrastructure sectors
Social aspect:
- General need to ensure the public safety of democratic processes inside the EU (avoiding Elections Interference and other negative ideology-driven societal impacts)
- The more informed and trusted decision-making process in cybersecurity
- Early-stage cybersecurity threats detection, prediction and response capability
- Capability to tackle complex cybersecurity threats (Full spectrum, Multi-Stage, Unique, long-term, APT’s)
Benefits for EU:
- EU cybersecurity institutions will have capabilities to address complex, advances cyber threats
- EU institutions will have capability will have the knowledge and capabilities to work with cyber threats (early phases of kill chain)
- Solutions developed in a targeted timeframe will put EU industries, SME’s, Academia into the lead position in this field.
Domain (JRC Taxonomy): Top-Tier Cybersecurity Threats
Sector (JRC Taxonomy): Defense, Governmental and public authorities, Public Safety as direct sectors
Relation to emerging technologies: Threats intelligence, All-data based analytics, Visual analytics, Predictive analytics of cyber threats
Trustworthy Software
2021-2029
Problem description
Overall challenge: gain trust in the security of software, either by construction or by validation. Security here is taken to mean that the software respects the confidentiality, integrity, and availability of data to be protected.
Industrial demand: Strong in many sectors, including banking, finance, transportation, energy, health.
Social aspect: Increase the confidence that end users have in the digital economy. Guarantee the protection of privacy.
Benefits for EU: Win a competitive edge in other industrial sectors by an increase in software productivity, security and certification.
Domain (JRC Taxonomy): Assurance, audit and certification. Software and hardware Security Engineering. Theoretical foundations.
Sector (JRC Taxonomy): Defense, Energy, Financial, Health, Nuclear, Transportation, Space.
Relation to emerging technologies: The emergence of quantum computing will raise additional questions of how to construct and validate software systems. Techniques developed for classical Trustworthy Software will need to be reviewed in light of this emerging paradigm.
User-Centric Data Governance
2022-2030
Problem description
Our connected world experiences unprecedented growth in terms of personal, increasingly intrusive data collection, be it while surfing the web, using a smartphone, or driving a connected car. At the same time, data protection regulation has evolved in Europe with the General Data Protection Regulation (GDPR) that came into effect on May 2018 to better protect the European Union resident in this connected world.
These evolutions raise three general types of questions. Certain questions are related to the privacy principles that need to be better understood and defined, like for instance, the notion of user control, of user empowerment, of user information.
Tools are also needed in several domains of privacy. For instance, the GDPR provides very little guidance about the effective implementation of some of the concepts it puts forward, like Data Protection Impact Assessments (DPIA). More generally, and independently of GDPR, a broad set of Privacy Enhancement Tools (PET) are required, from database anonymization technics (e.g., required by open-data initiatives) to various forms of privacy-preserving protocols (e.g., for unlinkability or anonymized communications).
Finally, the lack of transparency in our connected world, with many services and devices behaving as black boxes, and the lack of user control, are major issues. How to express consent or opposition in the absence of information or user interface? Identification of such hidden behaviours, which requires data flow analyses, is hindered by the number, complexity, and diversity of underlying applications and communication technologies. Challenging transverse research activities are required to bring transparency, highlight good and bad practices, and enable regulators to enforce data protection laws.
- Privacy protection technologies and tools: Privacy protection requires the setup and the use of a large number of technologies and tools (or PET, Privacy Enhancement Technologies). Some of these technologies are approaching maturity, while others (e.g., homomorphic encryption) remain so challenging that availability forecasts are almost impossible. Finally, certain technologies (e.g., anti-tracking tools for web browsing) are subject to constant evolutions, being subject to a cat-and-mouse game with companies responsible for these privacy leaks. For instance we can mention Attribute-Based Credentials, Blind signatures, Homomorphic encryption, PETs in Access Control, Privacy by standard cryptography, Pseudonymous systems, Proof of knowledge protocols, Secret sharing, Secure multi-party computation, Anonymizing networks, Anti-tracking tools, Onion routing, Data aggregation, Data acquisitions/collection, Database privacy, Data swapping, Generalization, Microdata protection, Obfuscation-based privacy, or Web privacy (anti-tracking technologies);
- Analysis of privacy threats and attacks: As in cryptography, where cryptanalysis (i.e., deliberate attacks) play a key role in assessing the security of cryptographic components, several PETs (see T.1) must be challenged by privacy researchers. For instance, de-anonymization attacks are key to assess the efficiency of database anonymization and thereby in bringing confidence in the related anonymization technologies. This category of activity also involves the practical analysis of several ecosystems, IoT or smart buildings being two examples. Many questions arise like what are the actors? What are the practices? What data is collected and to whom is it sent? What is the underlying economic model? For instance, we can mention Generic attacks to privacy, Location tracking, Malware based on privacy leakages, Data correlation, Data profiling, Information leakage, Location leakage, Side channels, Differential privacy, k-Anonymity concepts, or Measuring and quantifying privacy;
- Privacy Evaluation: Formal methods can play a key role in privacy evaluations of systems and services. For instance, it can be key in assessing architectures and being in a position to prove compliance with regulation, or to reason and assess the adequacy of privacy policies, or in performing Data Protection Impact Assessment. For instance, we can mention Model definitions, Policy languages and tools for privacy, Data Protection Impact Assessment tools, Evaluation of PETs in systems, or Audits;
- Privacy-preserving management and regulations: Regulation plays a key role in personal data protection. However, the regulation defines generic concepts (e.g., a user control) that often need to be further defined, taking into account various dimensions (e.g., technical, human, legal, economic). The regulation also requires a data controller to perform privacy risks analysis, or be accountable for his actions, which further raises additional questions (e.g., keeping records of actions performed without creating additional privacy risks). Other aspects, like usability, control, consent, or information, also play a key role in the privacy landscape. For instance, we can mention Concept and design strategies, Human factors, usability and user-centered design for PETs, Personal data life cycle, PETs controls matrix, Privacy by design, Privacy principles of ISO/IEC 29100, Consent mechanisms, Compliance with regulations, Legal regulations, National laws related to privacy in EU and rest of World, or Privacy policy enforcement.
Industrial demand:
- Any business has to conform to the GDPR. Understanding the concepts, having at our disposal practical tools, having open, accountable, secure and private-by-design procedures are mandatory.
- Beyond the legal aspect, it is the long-term interest of private companies to improve their relationships with their clients. Improving trust in the products and services that are provided is key for sustainable relationships, in a context of massive data collection. Bringing transparency, accountability and control to the end-users are key aspects.
Social aspect:
- The user trust in the digital, connected world is key to its acceptance. Without trust, digital evolution runs the risk of being subject to a major rejection.
- The end-user is often inclined to declare herself concerned by privacy while at the same time behaving in an opposite manner. This well-known “privacy paradox” highlights the need for sociological studies to better understand human behaviours in this domain and potentially improve awareness and practices.
Benefits for EU:
- Promote the European values relative to digital rights, and thus promote the European model of data protection.
- Enhance the European offer in terms of Privacy Enhancement Tools.
- Continue to be an international leader in terms of data protection.
- Favour the success of companies that promote privacy as a key differentiator with respect to non-European competitors.
Domain (JRC Taxonomy): Data security and privacy
Sector (JRC Taxonomy): Potentially all (perhaps except nuclear)
Relation to emerging technologies: With the advent of IoT, privacy leaks may reach an unprecedented level in volume and precision, both within the digital and physical worlds, and often without the user’s knowledge.
Autonomous Security for Self-Protected Systems
2019-2030
Problem description
With the constant and significant increase in the speed with which attacks spread or are able to spread, it has become crucial on the one hand to be able to detect these attacks in real-time, and on the other hand to be able to diagnose these attacks in order to consider in fine the automatic implementation of countermeasures.
Industrial demand:
- Any business has to protect itself against potential attacks. This is a difficult and costly task. Automation would simplify this task and reduce its cost.
- Autonomous security is not currently operative. This is a subject on which Europe could take the research and then industrial lead.
Social aspect: Security and Privacy are two major concerns for the general public. The demand for secure computing environment is huge, both in the professional and in the personal sphere. Nevertheless, the mandatory skills are rare. Addressing this problem represents a long term effort in education and training. If bringing a better training to more people is crucial, automation may also be viewed as a way to tackle the problem.
Benefits for EU: The global geostrategic context is bad, as we all know, and Europe is facing powerful countries (USA, China, Russia). In this context, a "cyberwar" cannot be ruled out. Even without going that far, the protection of our European industrial assets is also necessary. The role of human operators remains of course major for cyber defense, but it is conceivable that in the near future there will be so many (maybe automated) attacks (i.e., a cyber-hurricane) that the automation of at least part of the response will be just essential to survive.
Domain (JRC Taxonomy): Operational Incident Handling and Digital Forensics
Sector (JRC Taxonomy): Potentially all, with special importance in Energy, Transportation, Digital Infrastructure, Finance, Supply Chain
Relation to emerging technologies: We cannot totally exclude, even if for the time being the feasibility remains an issue, that AI-based systems could be able to autonomously handle advanced attack campaigns in the future. Faced with such automated attacks, a human response could be totally ineffective. Consequently, the automation of the response (at least defensively, as proposed here) will be a necessity.
Quantum Information Technology
2024-2030
Problem description
Quantum theory is entering the area of information technology. Quantum communication is emerging as a technology and it is likely that building a universal quantum computer will become feasible in the next decades. This raises several questions in terms of cybersecurity: how can quantum communication help to improve cybersecurity and, conversely what are the security threats bring by this new way of computing? Similarly, how much does it cost to migrate to quantum resistant technologies?
Industrial demand:
- Industry needs a secure way for communication and protection of its sensitive data
- Quantum computers once implemented will threaten the existing cryptographic schemas. The industry needs new cryptographic schemas strong enough to withstands quantum adversary. In addition, those technologies need to be embedded in legacy systems.
- Quantum technology is appealing for implementation, but must be carefully incorporated in the existing classical networks, to ensure that all risks are well understood and properly treated.
Social aspect: Quantum information technology is both opportunity for stronger security and dangerous threat for it. It especially targets the existing cryptographic systems which ensure confidentiality of private data, as well as integrity of most transactions. Access of the society to the digital services will be severely impacted, significantly reducing the public trust in digital economy.
Benefits for EU: It is difficult to overestimate possible benefits for EU from possessing quantum information technologies. Industry and society will be severely impacted if this technology is not timely and correctly implemented. Loosing quantum race may put a country in a weak position with respect to the winner, threatening the work of security and intelligence agencies, ability to protect basic human rights, correctness of operation of governmental institutes, etc.
Domain (JRC Taxonomy): Cryptology; Security Management and Governance; Network and Distributed Systems
Sector (JRC Taxonomy): All
Relation to emerging technologies: Quantum computing is by itself an emerging technology, which is only recently proved to be soon implemented in practices. Some cutting edge cryptographic techniques could be outlined here, like lattice-based, code-based, and multivariate-based primitives.
5G Security
2022-2030
Problem description
5G technology does not only provide a new, faster and more reliable communication facilities, it also opens the possibility for much higher amount of (sensitive) data to be transferred, connecting different types of infrastructure and applying novel technologies. These data should be protected from the possible abuse by malicious technology and software providers or dishonest network facility providers.
Industrial demand:
- Industry will rely on 5G networks to share its sensitive data
- 5G providers will have to ensure a high level of protection for their customers and cooperate with other similar providers with different level of security.
- 5G providers will rely on (untrusted) 5G technology providers and would like to be assured that proper quality of protection is provided and the applied solution do not violate security requirements.
Social aspect: 5G will have huge impact on the life of the generic public. Clearly, personal data will be exchanged between users and industry and processed further. As with growing reliance of the public on IT services the demand for privacy raises, the pressure on communication providers to protect the data in transfer is increasing as well. Thus, security of the 5G technologies will have immense impact on the trust in IT technology in general.
Benefits for EU: Apart of direct benefit for the European industry in increasing the competitiveness of their 5G technological solutions, the following benefits should be also outlined. First of all, this will let the EU to be able to protect and control its data, ensuring that the basic rights of its citizens are guaranteed and the EU laws are enforced. Good knowledge of 5G security will also ensure that the technologies adapted by EU industry from external technology providers is genuine, free from possible backdoors and complies with EU standards and regulations. High level of security of 5G communication networks will also increase the trust of citizens and business in the IT technologies, as well as in the EU’s capability to protect its values.
Domain (JRC Taxonomy): Assurance, Audit, and Certification; Security Management and Governance; Network and Distributed Systems; Software and Hardware Security Engineering; Cryptology
Sector (JRC Taxonomy): Digital Infrastructure, Supply Chain.
Relation to emerging technologies: 5G network uses various cutting edge technologies for providing the most up-to-date and long lasting communication service. Thus, it employs Cloud Computing, Artificial Intelligence, IoT technologies, as well as Software Defined Networks, Network Function Virtualization, Multiple-Input and Multiple-Output, etc. The usage of these cutting edge technologies results in a number of benefits for the new generation network, but also causes a number of problems for security because of increased attack surface, which may (and, most probably, will) expand in the future.